Sunday, October 31, 2010
Tuesday, June 29, 2010
differences between internet,intranet and extranet
There's one major distinction between an intranet and the Internet: The Internet is an open, public space, while an intranet is designed to be a private space. An intranet may be accessible from the Internet, but as a rule it's protected by a password and accessible only to employees or other authorized users. From within a company, an intranet server may respond much more quickly than a typical Web site. This is because the public Internet is at the mercy of traffic spikes, server breakdowns and other problems that may slow the network. Within a company, however, users have much more bandwidth and network hardware may be more reliable. This makes it easier to serve high bandwidth content, such as audio and video, over an intranet. (unless you work for the United States Marine Corps. Then you don't get to watch video's. And they Block 80% of any kind of "fun" or entertaining website available on the Internet) The Extranet is a portion of an organization's Intranet that is made accessible to authorized outside users without full access to an entire organization's intranet.
Posted by niney at 7:16 PM 0 comments
Sunday, June 20, 2010
network topology
Network topology is defined as the interconnection of the various elements (links, nodes, etc.) of a computer network.[1][2] Network Topologies can be physical or logical. Physical Topology means the physical design of a network including the devices, location and cable installation. Logical topology refers to the fact that how data actually transfers in a network as opposed to its physical design.
Topology can be considered as a virtual shape or structure of a network. This shape actually does not correspond to the actual physical design of the devices on the computer network. The computers on the home network can be arranged in a circle shape but it does not necessarily mean that it presents a ring topology.
Any particular network topology is determined only by the graphical mapping of the configuration of physical and/or logical connections between nodes. The study of network topology uses graph theory. Distances between nodes, physical interconnections, transmission rates, and/or signal types may differ in two networks and yet their topologies may be identical.
A Local Area Network (LAN) is one example of a network that exhibits both a physical topology and a logical topology. Any given node in the LAN has one or more links to one or more nodes in the network and the mapping of these links and nodes in a graph results in a geometrical shape that may be used to describe the physical topology of the network. Likewise, the mapping of the data flow between the nodes in the network determines the logical topology of the network. The physical and logical topologies may or may not be identical in any particular network.
Posted by niney at 6:41 PM 0 comments
network architecture

In computing, the network architecture is a characteristics of a computer network. The most prominent architecture today is evident in the framework of the Internet, which is based on the Internet Protocol Suite.
In telecommunication, the specification of a network architecture may also include a detailed description of products and services delivered via a communications network, as well as detailed rate and billing structures under which services are compensated.
In distinct usage in distributed computing, network architecture is also sometimes used as a synonym for the structure and classification of distributed application architecture, as the participating nodes in a distributed application are often referred to as a network. For example, the applications architecture of the public switched telephone network (PSTN) has been termed the Advanced Intelligent Network. There are any number of specific classifications but all lie on a continuum between the dumb network (e.g., Internet) and the intelligent computer network (e.g., the telephone network). Other networks contain various elements of these two classical types to make them suitable for various types of applications. Recently the context aware network, which is a synthesis of the two, has gained much interest with its ability to combine the best elements of both.
Posted by niney at 6:32 PM 0 comments
computer network
A computer network allows sharing of resources and information among devices connected to the network. The Advanced Research Projects Agency (ARPA) funded the design of the Advanced Research Projects Agency Network (ARPANET) for the United States Department of Defense. It was the first operational computer network in the world.[1] Development of the network began in 1969, based on designs developed during the 1960s. For a history see ARPANET, the first network.
[edit] Purpose
Computer networks can be used for several purposes:
Facilitating communications. Using a network, people can communicate efficiently and easily via e-mail, instant messaging, chat rooms, telephony, video telephone calls, and videoconferencing.
Sharing hardware. In a networked environment, each computer on a network can access and use hardware on the network. Suppose several personal computers on a network each require the use of a laser printer. If the personal computers and a laser printer are connected to a network, each user can then access the laser printer on the network, as they need it.
Sharing files, data, and information. In a network environment, any authorized user can access data and information stored on other computers on the network. The capability of providing access to data and information on shared storage devices is an important feature of many networks.
Sharing software. Users connected to a network can access application programs on the network.
Posted by niney at 6:28 PM 0 comments
Thursday, June 3, 2010
Information systems
An Information System (IS) is any combination of information technology and people's activities using that technology to support operations, management, and decision-making.[1] In a very broad sense, the term information system is frequently used to refer to the interaction between people, algorithmic processes, data and technology. In this sense, the term is used to refer not only to the information and communication technology (ICT) an organization uses, but also to the way in which people interact with this technology in support of business processes[2].
Some make a clear distinction between information systems, ICT and business processes. Information systems are distinct from information technology in that an information system is typically seen as having an ICT component. Information systems are also different from business processes. Information systems help to control the performance of business processes [3].
Alter argues for an information system as a special type of work system. A work system is a system in which humans and/or machines perform work using resources (including ICT) to produce specific products and/or services for customers. An information system is a work system whose activities are devoted to processing (capturing, transmitting, storing, retrieving, manipulating and displaying) information [4].
Part of the difficulty in defining the term information system is due to vagueness in the definition of related terms such as system and information. Beynon-Davies argues for a clearer terminology based in systemics and semiotics. He defines an information system as an example of a system concerned with the manipulation of signs. An information system is a type of socio-technical system. An information system is a mediating construct between actions and technology [5].
As such, information systems inter-relate with data systems on the one hand and activity systems on the other. An information system is a form of communication system in which data represent and are processed as a form of social memory. An information system can also be considered a semi-formal language which supports human decision making and action.
Information systems are the primary focus of study for the information systems discipline and for organisational informatics[6].
Posted by niney at 1:21 AM 0 comments
programme development phase
To make a program, the programmer has to undergo several phases and which will determine how and what the program he should make.
Firstly, the programmer has to undergo the analyzing phase. In this phase, the programmer has to conduct a survey to determine the problem faced by the client and know the target user.
Then, the programmer will begin the design phase. In the design phase, the programmer has to design the program and draw them out as a pseudo code, flow chart or top down design model.
Next is the coding phase. In the coding phase, the programmer will begin his work on coding the program. The coding is usually be done by several programmer as a complex program consist of many syntax.
Testing and debugging phase are the next phase. Here the program done will be tested to ensure that is error free. The usual error is the syntax error, logic error and run-time error. This phase is also called debugging because the error occurred are also known as bug.
Finally it is the documentation phase. Documentation is also including internal documentation and marketing documentation. Internal documentation is made so that the programmer can easily edit the code in the future. It also enables other programmer to know how the program is coded so that they can also improve it. Marketing documentation is done so that the customer can have a better understanding on the program. This will also enable the potential customer to compare the program with other product and expect what they could gain from the program.
Posted by niney at 1:19 AM 0 comments
Tuesday, June 1, 2010
Programing process
IntroductionComputer programs are collections of instructions that tell a computer how to interact with the user, interact with the computer hardware and process data. The first programmable computers required the programmers to write explicit instructions to directly manipulate the hardware of the computer. This "machine language" was very tedious to write by hand since even simple tasks such as printing some output on the screen require 10 or 20 machine language commands. Machine language is often referred to as a "low level language" since the code directly manipulates the hardware of the computer.By contrast, higher level languages such as "C", C++, Pascal, Cobol, Fortran, ADA and Java are called "compiled languages". In a compiled language, the programmer writes more general instructions and a compiler (a special piece of software) automatically translates these high level instructions into machine language. The machine language is then executed by the computer. A large portion of software in use today is programmed in this fashion.We can contrast compiled programming languages with interpreted programming languages. In an interpreted programming language, the statements that the programmer writes are interpreted as the program is running. This means they are translated into machine language on the fly and then execute as the program is running. Some popular interpreted languages include Basic, Visual Basic, Perl and shell scripting languages such as those found in the UNIX environment.We can make another comparison between two different models of programming. In structured programming, blocks of programming statements (code) are executed one after another. Control statements change which blocks of code are executed next.In object oriented programming, data are contained in objects and are accessed using special methods (blocks of code) specific to the type of object. There is no single "flow" of the program as objects can freely interact with one another by passing messages.In this tutorial, we focus only on structured programming.Program StructureVirtually all structured programs share a similar overall structure:Statements to establish the start of the programVariable declarationProgram statements (blocks of code)The following is a simple example of a program written in several different programming languages. We call this the "Hello World" example since all the program does is print "Hello World" on the computer screen.LanguageExample program"C"#includevoid main() {printf("Hello World");}C++#includeint main(){coutPascalprogram helloworld (output);beginwriteln('Hello World');end.Oracle PL/SQLCREATE OR REPLACE PROCEDURE helloworld ASBEGINDBMS_OUTPUT.PUT_LINE('Hello World');END;Javaclass helloworld{public static void main (String args []){System.out.println ("Hello World");}}Perl#!/usr/local/bin/perl -wprint "Hello World";Basicprint "Hello World"
Posted by niney at 7:52 PM 0 comments
Multimedia introduction
1 INTRODUCTIONAs the name suggests, multimedia is a set of more than one media element used to produce a concrete and more structured way of communication. In other words multimedia is simultaneous use of data from different sources. These sources in multimedia are known as media elements. With growing and very fast changing information technology, Multimedia has become a crucial part of computer world. Its importance has realised in almost all walks of life, may it be education, cinema, advertising, fashion and what not.Throughout the 1960s, 1970s and 1980s, computers have been restricted to dealing with two main types of data - words and numbers. But the cutting edge of information technology introduced faster system capable of handling graphics, audio, animation and video. And the entire world was taken aback by the power of multimedia.35.2 OBJECTIVESAfter going through this lesson you should be able toexplain what is multimediaunderstand the importance of individual media elementsidentify different hardware components required to run a multimediaappreciate the impact of audio in educational presentationdescribe how visual images, graphics and audio can be added to a presentationenhance the capability of multimedia through interactive video impact35.3 WHAT IS MULTIMEDIA?Multimedia is nothing but the processing and presentation of information in a more structured and understandable manner using more than one media such as text, graphics, animation, audio and video. Thus multimedia products can be an academic presentation, game or corporate presentation, information kiosk, fashion-designing etc. Multimedia systems are those computer platforms and software tools that support the interactive uses of text, graphics, animation, audio, or motion video. In other words, a computer capable of handling text, graphics, audio, animation and video is called multimedia computer. If the sequence and timing of these media elements can be controlled by the user, then one can name it as Interactive Multimedia.35.4 DIFFERENT MEDIA ELEMENTS(i) TextInclusion of textual information in multimedia is the basic step towards development of multimedia software. Text can be of any type, may be a word, a single line, or a paragraph. The textual data for multimedia can be developed using any text editor. However to give special effects, one needs graphics software which supports this kind of job. Even one can use any of the most popular word processing software to create textual data for inclusion in multimedia. The text can have different type, size, color and style to suit the professional requirement of the multimedia software.(ii) GraphicsAnother interesting element in multimedia is graphics. As a matter of fact, taking into consideration the human nature, a subject is more explained with some sort of pictorial/graphical representation, rather than as a large chunk of text. This also helps to develop a clean multimedia screen, whereas use of large amount of text in a screen make it dull in presentation.Unlike text, which uses a universal ASCII format, graphics does not have a single agreed format. They have different format to suit different requirement. Most commonly used format for graphics is .BMP or bitmap pictures. The size of a graphics depends on the resolution it is using. A computer image uses pixel or dots on the screen to form itself. And these dots or pixel, when combined with number of colors and other aspects are called resolution. Resolution of an image or graphics is basically the pixel density and number of colors it uses. And the size of the image depends on its resolution. A standard VGA (Virtual Graphics Arrays) screen can display a screen resolution of 640 ´ 480 = 307200 pixel. And a Super VGA screen can display up-to 1024 ´ 768 = 786432 pixel on the screen. While developing multimedia graphics one should always keep in mind the image resolution and number of colors to be used, as this has a direct relation with the image size. If the image size is bigger, it takes more time to load and also requires higher memory for processing and larger disk-space for storage.However, different graphics formats are available which take less space and are faster to load into the memory.There are several graphics packages available to develop excellent images and also to compress them so that they take lesser disk-space but use higher resolution and more colours. Packages like Adobe PhotoShop, Adobe Illustrator, PaintShop Pro etc. are excellent graphics packages. There are Graphics gallery available in CD’s (Compact Disk) with readymade images to suit almost every requirement. These images can directly be incorporated into multimedia development.(iii) AnimationMoving images have an overpowering effect on the human peripheral vision. Followings are few points for its popularity.Showing continuity in transitions:Animation is a set of static state, related to each other with transition. When something has two or more states, then changes between states will be much easier for users to understand if the transitions are animated instead of being instantaneous. An animated transition allows the user to track the mapping between different subparts through the perceptual system instead of having to involve the cognitive system to deduce the mappings.Indicating dimensionality in transitions:Sometimes opposite animated transitions can be used to indicate movement back and forth along some navigational dimension. One example used in several user interfaces is the use of zooming to indicate that a new object is "grown" from a previous one (e.g., a detailed view or property list opened by clicking on an icon) or that an object is closed or minimized to a smaller representation. Zooming out from the small object to the enlargement is a navigational dimension and zooming in again as the enlargement is closed down is the opposite direction along that dimension.Illustrating change over timeSince animation is a time-varying display, it provides a one-to-one mapping to phenomena that change over time. For example, deforestation of the rain forest can be illustrated by showing a map with an animation of the covered area changing over time.
Posted by niney at 7:50 PM 0 comments
Multimedia concepts
1 INTRODUCTIONAs the name suggests, multimedia is a set of more than one media element used to produce a concrete and more structured way of communication. In other words multimedia is simultaneous use of data from different sources. These sources in multimedia are known as media elements. With growing and very fast changing information technology, Multimedia has become a crucial part of computer world. Its importance has realised in almost all walks of life, may it be education, cinema, advertising, fashion and what not.Throughout the 1960s, 1970s and 1980s, computers have been restricted to dealing with two main types of data - words and numbers. But the cutting edge of information technology introduced faster system capable of handling graphics, audio, animation and video. And the entire world was taken aback by the power of multimedia.35.2 OBJECTIVESAfter going through this lesson you should be able toexplain what is multimediaunderstand the importance of individual media elementsidentify different hardware components required to run a multimediaappreciate the impact of audio in educational presentationdescribe how visual images, graphics and audio can be added to a presentationenhance the capability of multimedia through interactive video impact35.3 WHAT IS MULTIMEDIA?Multimedia is nothing but the processing and presentation of information in a more structured and understandable manner using more than one media such as text, graphics, animation, audio and video. Thus multimedia products can be an academic presentation, game or corporate presentation, information kiosk, fashion-designing etc. Multimedia systems are those computer platforms and software tools that support the interactive uses of text, graphics, animation, audio, or motion video. In other words, a computer capable of handling text, graphics, audio, animation and video is called multimedia computer. If the sequence and timing of these media elements can be controlled by the user, then one can name it as Interactive Multimedia.35.4 DIFFERENT MEDIA ELEMENTS(i) TextInclusion of textual information in multimedia is the basic step towards development of multimedia software. Text can be of any type, may be a word, a single line, or a paragraph. The textual data for multimedia can be developed using any text editor. However to give special effects, one needs graphics software which supports this kind of job. Even one can use any of the most popular word processing software to create textual data for inclusion in multimedia. The text can have different type, size, color and style to suit the professional requirement of the multimedia software.(ii) GraphicsAnother interesting element in multimedia is graphics. As a matter of fact, taking into consideration the human nature, a subject is more explained with some sort of pictorial/graphical representation, rather than as a large chunk of text. This also helps to develop a clean multimedia screen, whereas use of large amount of text in a screen make it dull in presentation.Unlike text, which uses a universal ASCII format, graphics does not have a single agreed format. They have different format to suit different requirement. Most commonly used format for graphics is .BMP or bitmap pictures. The size of a graphics depends on the resolution it is using. A computer image uses pixel or dots on the screen to form itself. And these dots or pixel, when combined with number of colors and other aspects are called resolution. Resolution of an image or graphics is basically the pixel density and number of colors it uses. And the size of the image depends on its resolution. A standard VGA (Virtual Graphics Arrays) screen can display a screen resolution of 640 ´ 480 = 307200 pixel. And a Super VGA screen can display up-to 1024 ´ 768 = 786432 pixel on the screen. While developing multimedia graphics one should always keep in mind the image resolution and number of colors to be used, as this has a direct relation with the image size. If the image size is bigger, it takes more time to load and also requires higher memory for processing and larger disk-space for storage.However, different graphics formats are available which take less space and are faster to load into the memory.There are several graphics packages available to develop excellent images and also to compress them so that they take lesser disk-space but use higher resolution and more colours. Packages like Adobe PhotoShop, Adobe Illustrator, PaintShop Pro etc. are excellent graphics packages. There are Graphics gallery available in CD’s (Compact Disk) with readymade images to suit almost every requirement. These images can directly be incorporated into multimedia development.(iii) AnimationMoving images have an overpowering effect on the human peripheral vision. Followings are few points for its popularity.Showing continuity in transitions:Animation is a set of static state, related to each other with transition. When something has two or more states, then changes between states will be much easier for users to understand if the transitions are animated instead of being instantaneous. An animated transition allows the user to track the mapping between different subparts through the perceptual system instead of having to involve the cognitive system to deduce the mappings.Indicating dimensionality in transitions:Sometimes opposite animated transitions can be used to indicate movement back and forth along some navigational dimension. One example used in several user interfaces is the use of zooming to indicate that a new object is "grown" from a previous one (e.g., a detailed view or property list opened by clicking on an icon) or that an object is closed or minimized to a smaller representation. Zooming out from the small object to the enlargement is a navigational dimension and zooming in again as the enlargement is closed down is the opposite direction along that dimension.Illustrating change over timeSince animation is a time-varying display, it provides a one-to-one mapping to phenomena that change over time. For example, deforestation of the rain forest can be illustrated by showing a map with an animation of the covered area changing over time.
Posted by niney at 7:43 PM 0 comments
Software requirements
A Software Requirements Specification (SRS) is a complete description of the behavior of the system to be developed. It includes a set of use cases that describe all the interactions the users will have with the software. Use cases are also known as functional requirements. In addition to use cases, the SRS also contains non-functional (or supplementary) requirements. Non-functional requirements are requirements which impose constraints on the design or implementation (such as performance engineering requirements, quality standards, or design constraints
Posted by niney at 7:40 PM 0 comments
Hardware requiments for network
IntroductionThis is a continuation of my series of articles on the terms and concepts that are frequently asked in IT interviews. This article is an attempt to discuss the salient terminologies and concepts related to Computer networking that are often asked in interviews. Although an article on Computer Networking concepts and terms would run for many pages, I have discussed only important ones to make it fit in one article.Computer NetworkA Computer Network implies two or more computers those are linked together through some software, hardware, etc for the purpose of exchanging data and information.InternetThe Internet is a network of networks. It is "the worldwide, publicly accessible network of interconnected computer networks that transmit data by packet switching using the standard Internet Protocol (IP)."World Wide Web The World Wide Web or WWW is a hypertext based distributed information system. It "is the global network of hypertext (HTTP) servers that allow text, graphics, audio and video files to be mixed together." It is an "information space in which the items of interest, referred to as resources, are identified by global identifiers called Uniform Resource Identifiers (URI)." According to Tim Berners-Lee, inventor of the World Wide Web, "The World Wide Web is the universe of network-accessible information, an embodiment of human knowledge."ModemA modem is a modulator-demodulator device that is used for converting the transmission signals from digital to analog for transmission over voice-grade phone lines. While the digital signals are converted to a form suitable for transmission over analog communication at the source, the reverse happens at the destination where these analog signals are returned to their original digital form.Network Interface ControllerA network card, network adapter or the Network Interface Controller (NIC) is a piece of computer hardware that facilitates the systems in a network to communicate.BroadcastingWhen the information transfer is from one system to many systems using the same means of transfer then such a network is known as a Broadcasting or Multicasting.UnicastingWhen the information transfer is from one system to any other single system using the same means of transfer then such a network is known as Point-to-Point or Unicasting.BandwidthNetwork bandwidth or network throughput is a measure of the data transfer rate or the amount of data that can pass through a network interface over a specific period of time. This is expressed in bits per second or bps.BroadbandThis is a wide-band technology that is capable of supporting voice, video and data. It is "a transmission medium capable of supporting a wide range of frequencies, typically from audio up to video frequencies. It can carry multiple signals by dividing the total capacity of the medium into multiple, independent bandwidth channels, where each channel operates only on a specific range of frequencies."Integrated Services Digital Network (ISDN)Integrated Services Digital Network, an international standard for end-to-end digital transmission of voice, data, and signaling facilitates very high-speed data transfer over existing phone lines.Network Load BalancingNetwork Load Balancing may be defined as a technique that "distributes the network traffic along parallel paths to maximize the available network bandwidth while providing redundancy."Local Area NetworkLAN also known as Local Area Network are networks restricted on the bases of the area they cover. These networks stretch around an area of 10 meters to 1 km. "LANs enabled multiple users in a relatively small geographical area to exchange files and messages, as well as access shared resources such as file servers and printers." The commonly used LAN devices include repeaters, hubs, LAN extenders, bridges, LAN switches, and routers.Metropolitan Area NetworkMAN also known, as Metropolitan Area Network is a network that is larger than LANs spreading across an area of 1 km to 10kms. A simple example for this type of network is the branches of a bank spread across the city and are connected for information exchange.Wide Area NetworkWAN also known, as Wide Area Network is a network that is larger than a MAN, it spreads across an area of 100kms to 1000 kms. "A WAN is a data communications network that covers a relatively broad geographic area and that often uses transmission facilities provided by common carriers, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer." A simple example for these networks is the network of a huge IT company, which contains branches all over the world with all its branches connected to each other.Wireless NetworksWireless Networks are those networks wherein the interconnection between two systems is not physical. The computers that interchange information are not physically linked with wires.BluetoothBluetooth is a wireless network that has a short range and can be used to connect a system with its internal components like monitor, mouse, CPU, etc without actually having a plug in. Components that support the Bluetooth technology can be detected whenever they are in the detectable range.RoutingWhen there are multiple paths between the sender and the receiver the best path for sending the information has to be chosen. The choice is made based on a number of criteria like the number of hops between the systems or on the physical distance between the systems. This process of finding the best path is known as routing.
Posted by niney at 7:37 PM 0 comments
Basic concept
IntroductionThis is a continuation of my series of articles on the terms and concepts that are frequently asked in IT interviews. This article is an attempt to discuss the salient terminologies and concepts related to Computer networking that are often asked in interviews. Although an article on Computer Networking concepts and terms would run for many pages, I have discussed only important ones to make it fit in one article.Computer NetworkA Computer Network implies two or more computers those are linked together through some software, hardware, etc for the purpose of exchanging data and information.InternetThe Internet is a network of networks. It is "the worldwide, publicly accessible network of interconnected computer networks that transmit data by packet switching using the standard Internet Protocol (IP)."World Wide Web The World Wide Web or WWW is a hypertext based distributed information system. It "is the global network of hypertext (HTTP) servers that allow text, graphics, audio and video files to be mixed together." It is an "information space in which the items of interest, referred to as resources, are identified by global identifiers called Uniform Resource Identifiers (URI)." According to Tim Berners-Lee, inventor of the World Wide Web, "The World Wide Web is the universe of network-accessible information, an embodiment of human knowledge."ModemA modem is a modulator-demodulator device that is used for converting the transmission signals from digital to analog for transmission over voice-grade phone lines. While the digital signals are converted to a form suitable for transmission over analog communication at the source, the reverse happens at the destination where these analog signals are returned to their original digital form.Network Interface ControllerA network card, network adapter or the Network Interface Controller (NIC) is a piece of computer hardware that facilitates the systems in a network to communicate.BroadcastingWhen the information transfer is from one system to many systems using the same means of transfer then such a network is known as a Broadcasting or Multicasting.UnicastingWhen the information transfer is from one system to any other single system using the same means of transfer then such a network is known as Point-to-Point or Unicasting.BandwidthNetwork bandwidth or network throughput is a measure of the data transfer rate or the amount of data that can pass through a network interface over a specific period of time. This is expressed in bits per second or bps.BroadbandThis is a wide-band technology that is capable of supporting voice, video and data. It is "a transmission medium capable of supporting a wide range of frequencies, typically from audio up to video frequencies. It can carry multiple signals by dividing the total capacity of the medium into multiple, independent bandwidth channels, where each channel operates only on a specific range of frequencies."Integrated Services Digital Network (ISDN)Integrated Services Digital Network, an international standard for end-to-end digital transmission of voice, data, and signaling facilitates very high-speed data transfer over existing phone lines.Network Load BalancingNetwork Load Balancing may be defined as a technique that "distributes the network traffic along parallel paths to maximize the available network bandwidth while providing redundancy."Local Area NetworkLAN also known as Local Area Network are networks restricted on the bases of the area they cover. These networks stretch around an area of 10 meters to 1 km. "LANs enabled multiple users in a relatively small geographical area to exchange files and messages, as well as access shared resources such as file servers and printers." The commonly used LAN devices include repeaters, hubs, LAN extenders, bridges, LAN switches, and routers.Metropolitan Area NetworkMAN also known, as Metropolitan Area Network is a network that is larger than LANs spreading across an area of 1 km to 10kms. A simple example for this type of network is the branches of a bank spread across the city and are connected for information exchange.Wide Area NetworkWAN also known, as Wide Area Network is a network that is larger than a MAN, it spreads across an area of 100kms to 1000 kms. "A WAN is a data communications network that covers a relatively broad geographic area and that often uses transmission facilities provided by common carriers, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer." A simple example for these networks is the network of a huge IT company, which contains branches all over the world with all its branches connected to each other.Wireless NetworksWireless Networks are those networks wherein the interconnection between two systems is not physical. The computers that interchange information are not physically linked with wires.BluetoothBluetooth is a wireless network that has a short range and can be used to connect a system with its internal components like monitor, mouse, CPU, etc without actually having a plug in. Components that support the Bluetooth technology can be detected whenever they are in the detectable range.RoutingWhen there are multiple paths between the sender and the receiver the best path for sending the information has to be chosen. The choice is made based on a number of criteria like the number of hops between the systems or on the physical distance between the systems. This process of finding the best path is known as routing.
Posted by niney at 7:35 PM 0 comments
Function OS
The main functions of an OS include:In a multitasking operating system where multiple programs can be running at the same time, the operating system determines which applications should run in what order and how much time should be allowed for each application before giving another application a turn.It manages the sharing of internal memory among multiple applications.It handles and monitors input and output to and from attached hardware devices, such as hard disks, printers, and dial-up ports. [8]It sends messages to each application or interactive user (or to a system operator) about the status of operation and any errors that may have occurred.It can offload the management of what are called batch jobs (for example, printing) so that the initiating application is freed from this work.On computers that can provide parallel processing, an operating system can manage how to divide the program so that it runs on more than one processor at a time.Scheduling the activities of the CPU and resources to achieve efficiency and prevention of deadlock
Posted by niney at 7:32 PM 0 comments
Operating system
An operating system is the software on a computer that manages the way different programs use its hardware, and regulates the ways that a user controls the computer.[1][2] Operating systems are found on almost any device that contains a computer with multiple programs—from cellular phones and video game consoles to supercomputers and web servers. Some popular modern operating systems for personal computers include Microsoft Windows, Mac OS X, and Linux[3] (see also: list of operating systems, comparison of operating systems).Because early computers were often built for only a single task, operating systems did not exist in their proper form until the 1960s.[4] As computers evolved into being devices that could run different programs in succession, programmers began putting libraries of common programs (in the form of computer code) onto the computer in order to avoid duplication and speed up the process. Eventually, computers began being built to automatically switch from one task to the next. The creation of runtime libraries to manage processing and printing speed came next, which evolved into programs that could interpret different types of programming languages into machine code. When personal computers by companies such as Apple Inc., Atari, IBM and Amiga became popular in the 1980s, vendors began adding features such as software scheduling and hardware maintenance.An operating system can be divided into many different parts. One of the most important parts is the kernel, which controls low-level processes that the average user usually cannot see: it controls how memory is read and written, the order in which processes are executed, how information is received and sent by devices like the monitor, keyboard and mouse, and deciding how to interpret information received by networks. The user interface is the part of the operating system that interacts with the computer user directly, allowing them to control and use programs. The user interface may be graphical with icons and a desktop, or textual, with a command line. Another similar feature is an Application programming interface, which is a set of services and code libraries that let applications interact with one another, as well as the operating system itself. Depending on the operating system, many of these components may not be considered an actual part. For example, Windows considers its user interface to be part of the operating system, while many versions of Linux do not.
Posted by niney at 7:29 PM 0 comments
Secondary storage
Secondary storage (or external memory) differs from primary storage in that it is not directly accessible by the CPU. The computer usually uses its input/output channels to access secondary storage and transfers the desired data using intermediate area in primary storage. Secondary storage does not lose the data when the device is powered down—it is non-volatile. Per unit, it is typically also two orders of magnitude less expensive than primary storage. Consequently, modern computer systems typically have two orders of magnitude more secondary storage than primary storage and data is kept for a longer time there.In modern computers, hard disk drives are usually used as secondary storage. The time taken to access a given byte of information stored on a hard disk is typically a few thousandths of a second, or milliseconds. By contrast, the time taken to access a given byte of information stored in random access memory is measured in billionths of a second, or nanoseconds. This illustrates the very significant access-time difference which distinguishes solid-state memory from rotating magnetic storage devices: hard disks are typically about a million times slower than memory. Rotating optical storage devices, such as CD and DVD drives, have even longer access times. With disk drives, once the disk read/write head reaches the proper placement and the data of interest rotates under it, subsequent data on the track are very fast to access. As a result, in order to hide the initial seek time and rotational latency, data are transferred to and from disks in large contiguous blocks.When data reside on disk, block access to hide latency offers a ray of hope in designing efficient external memory algorithms. Sequential or block access on disks is orders of magnitude faster than random access, and many sophisticated paradigms have been developed to design efficient algorithms based upon sequential and block access . Another way to reduce the I/O bottleneck is to use multiple disks in parallel in order to increase the bandwidth between primary and secondary memory.[2]Some other examples of secondary storage technologies are: flash memory (e.g. USB flash drives or keys), floppy disks, magnetic tape, paper tape, punched cards, standalone RAM disks, and Iomega Zip drives.The secondary storage is often formatted according to a file system format, which provides the abstraction necessary to organize data into files and directories, providing also additional information (called metadata) describing the owner of a certain file, the access time, the access permissions, and other information.Most computer operating systems use the concept of virtual memory, allowing utilization of more primary storage capacity than is physically available in the system. As the primary memory fills up, the system moves the least-used chunks (pages) to secondary storage devices (to a swap file or page file), retrieving them later when they are needed. As more of these retrievals from slower secondary storage are necessary, the more the overall system performance is degraded.
Posted by niney at 7:26 PM 0 comments
Primary storage
Posted by enny efafiqa at 5:28 PM 0 comments
Posted by niney at 7:21 PM 0 comments
Storage
Wednesday, May 19, 2010
Storage
Computer data storage, often called storage or memory, refers to computer components, devices, and recording media that retain digital data used for computing for some interval of time. Computer data storage provides one of the core functions of the modern computer, that of information retention. It is one of the fundamental components of all modern computers, and coupled with a central processing unit (CPU, a processor), implements the basic computer model used since the 1940s.In contemporary usage, memory usually refers to a form of semiconductor storage known as random-access memory (RAM) and sometimes other forms of fast but temporary storage. Similarly, storage today more commonly refers to mass storage — optical discs, forms of magnetic storage like hard disk drives, and other types slower than RAM, but of a more permanent nature. Historically, memory and storage were respectively called main memory and secondary storage. The terms internal memory and external memory are also used.The contemporary distinctions are helpful, because they are also fundamental to the architecture of computers in general. The distinctions also reflect an important and significant technical difference between memory and mass storage devices, which has been blurred by the historical usage of the term storage. Nevertheless, this article uses the traditional nomenclature.
Posted by enny efafiqa at 5:22 PM
Posted by niney at 7:20 PM 0 comments
Wednesday, April 28, 2010
Instalation anti virus
Install anti-virus software
Prevent virus infections
Anti-virus software is one of the main defences against online problems. It continually scans for viruses, including Trojans and worms. To be effective it must be kept up-to-date.
Why install anti-virus software?
Without anti-virus software you are very vulnerable to computer viruses, including:
Infected email attachments.
Drive-by infections caused by visiting corrupt websites.
Viruses that attack over the internet (“worms”).
Spyware that is introduced by virus infections.
Viruses that are spread using macros in application documents.
Depending on the software you use, it may detect some (but not all) spyware.
Being infected by a virus can have very serious consequences including:
Identity theft.
Fraud.
Loss of data.
A slow or unusable computer.
What anti-virus software does
Anti-virus software covers the main lines of attack:
It scans incoming emails for attached viruses.
It monitors files as they are opened or created to make sure they are not infected.
It performs periodic scans of every file on the computer.
What anti-virus software does NOT do
Anti-virus software will not protect you against:
Programs that you choose to install that may contain unwanted features.
Spam.
Against any kind of fraud or criminal activity online.
A hacker trying break into your computer over the internet.
It is not effective if it is switched off for any reason.
It is less effective (and mostly useless) if it is not kept up-to-date with the latest virus signatures.
A virus signature is like a criminal’s mugshot. Each time a new virus is released, security firms analyse it and create a new signature that lets anti-virus software block the new virus.
How to choose anti-virus software
For personal and home office use there are a number of basic choices that you can take to decide which anti-virus software to buy.
Standalone anti-virus or security suite?
Most anti-virus software companies sell a standalone program that only scans for viruses as well as security suite packages that include other protective software such as a firewall, spam filtering, anti-spyware and so on.
Generally the standalone packages cost around £20 and full suites run from £40-50.
Advantages of a suite: a suite should cover all the bases, share a single user interface and be easier and cheaper than buying each individual program separately.
Drawbacks: while the anti-virus component should be good, sometimes the other elements in a suite aren’t as good as the best of breed software from other suppliers. Also, some of the other components may be available for free.
For beginners, it is probably best to buy a suite.
For more sophisticated users, consider a pick-and-mix approach and buy a standalone anti-virus product (but don’t forget the other defences).
Free or commercial?
There are a number of anti-virus products that are free for personal or non-commercial use.
In most cases, these ‘free’ products are scaled-back versions of commercial products to which the software manufacturer hopes you will, one day, upgrade.
Advantages: price.
Drawbacks include: limited or no technical support; reduced functionality, for example in scheduling full scans; not from market-leading brands.
Unless getting free software is critical, it is preferable to buy a fully-supported commercial product.
Download free evaluation software
Several software developers offer free downloadable trial versions of their software that range from 3 to 12 months. A list of links to the download pages is available on Microsoft’s website.
How to evaluate anti-virus software
The main criteria are:
Price.
Review on reputable technical websites such as Cnet.
How easy it is to set up and use.
Level and quality of technical support, including the support website.
Frequency and responsiveness of signature updates. This is hard for most people to evaluate but well-known and reputable software companies should be okay.
How to buy anti-virus software
Then it is a matter of buying it or downloading it. Suppliers include: high street retailers, online retailers or direct purchase and download from the software developers over the internet.
Business anti-virus software
For networks of five or more computers and for business use, you should consider business versions of popular anti-virus software that are designed to make installation, updating and management easier on multiple computers.
Posted by niney at 6:21 PM 0 comments
Instalation Office 2007
How to install individual 2007 Office features
loadTOCNode(2, 'moreinformation');
Typically, when you first try to use a feature that is not installed, the 2007 Office program installs the feature automatically. If the feature that you want is not automatically installed, follow these steps:
Exit all programs.
Click Start, and then click Control Panel.
If you are running Microsoft Windows Vista or Microsoft Windows 7, do the following:
Click Programs, and then click Uninstall a Program.
Click the name of the Microsoft Office Edition 2007 you want to change, and then click Change. In this item, Edition is a placeholder for the edition of Office that you installed.Note In Classic view on Windows Vista or in Icon View on Windows 7, double-click Programs and Features, click the name of the Microsoft Office Edition 2007 you want to change, and then click Change.If you are running Microsoft Windows XP, do the following:
Click Add or Remove Programs.
Click the name of the Microsoft Office Edition 2007 you want to change, and then click Change.Note In Classic view, double-click Add or Remove Programs, click the name of the Microsoft Office Edition 2007 you want to change, and then click Change.
Back to the top
How to repair problems in the installed 2007 Office programs and features
loadTOCNode(2, 'moreinformation');
You can use either of the following methods to detect and to repair problems that are associated with installed Microsoft Office programs and features, such as registry settings and missing installation files. You cannot use these methods to repair personal files.
Method 1: Run Office Diagnostics from a 2007 Office program
loadTOCNode(3, 'moreinformation');
Start the Office Diagnostics tool. To do this, use either of the following methods:
For a menu-based 2007 Office program, click Office Diagnostics on the Help menu.
For a ribbon-based 2007 Office program, follow these steps:
Click the Microsoft Office Button, and then click Program Options.Note In this option, Program represents the name of the program.
In the Navigation Pane, click Resources.
Click Diagnose.
Click Continue.
Click Start Diagnostics. If the Office Diagnostics tool identifies a problem, it tries to fix the problem.
When the Office Diagnostics tool finishes, click Close.Note If you cannot run Office Diagnostics from a 2007 Office program, see the "How to run Office Diagnostics from the Start menu" in the Reference section.
Method 2: Run the Detect and Repair tool from Add or Remove Programs
loadTOCNode(3, 'moreinformation');
Click Start, and then click Control Panel.
If you are running Microsoft Windows Vista or Microsoft Windows 7, do the following:
Click Programs, and then click Uninstall a Program.
Click the name of the Microsoft Office Edition 2007 you want to change, and then click Change.
Click Repair, and then click Continue. Note In Classic view on Windows Vista or in Icon View on Windows 7, double-click Programs and Features. Click the name of the Microsoft Office Edition 2007 you want to change, and then click Change. Click Repair, and then click Continue.If you are running Microsoft Windows XP, do the following:
Click Add or Remove Programs.
Click the name of the Microsoft Office Edition 2007 you want to change, and then click Change.
Click Repair, and then click Continue. Note In Classic view, double-click Add or Remove Programs, click the name of the Microsoft Office Edition 2007 you want to change, and then click Change. Click Repair, and then click Continue.
Posted by niney at 6:19 PM 0 comments
Menformat hardisk
A. Langkah dan Tahap Format Ulang Hard Disk
1. Back up / bekap file penting anda yang ada pada hardisk karena dengan format akan menghapus semua file yang ada di hard disk anda. Jika anda punya cd-rw drive atau dvd-rw drive anda bisa membakar file anda ke dalam cd atau dvd. Cara lain backup adalah dengan flash disk, disket floppy, disket zip, pindah file ke jaringan network lan atau internet pada komputer atau server lain dan lain-lain.
2. Setelah backup selanjutnya adalah membuat windows boot disk / rescue disk pada disket floppy 1.4 MB. Disket ini bertujuan untuk booting langsung ke disket tidak melalui harddisk anda. Istilahnya anda akan menggunakan os microsoft dos yang ada pada disket yang anda buat.
3. Ganti Setting BiosSaat komputer dinyalakan anda harus langsung masuk ke tampilan bios untuk setting pilihan urutan boot. Caranya ketika komputer baru dinyalakan anda menekan dan menahan tombol delete sampai bios muncul di layar monitor komputer anda. Ganti urutan booting dengan urutan pertama floppy disk.
4. Format Hard DiskSetelah bios diganti serta disave anda masukkan disket kemudian restart komputer anda. Nanti komputer anda akan otomatis boot dari disket tersebut dan pilih boot without cd-rom supaya proses booting bisa lebih cepat. Setelah masuk ke command prompt a:\ ketik format c: lalu tekan enter. Disesuaikan dengan jumlah partisi anda yang ada. Jika anda punya partisi 3 buah maka tambah perintah format d: dan format e:. Tips dan cara mempartisi hard disk mungkin bisa anda cari di kotak search di sebelah kiri halaman artikel ini. Jika format telah selsesai beri nama drive tersebut sesuai selera anda. Jika semua beres dan berjalan lancar maka proses format ulang telah selesai. Kini harddisk anda menjadi seperti baru kembali.
B. Langkah dan Tahap Install Ulang OS Windows dan Linux
1. Install Windows 98 / 2000 / ME / XP / Vista / LinuxLangkah pertama dalam mengistall ulang operating system pada komputer pc atau laptop anda adalah booting ulang ke disket anda dan pilih support cd-rom device. Setelah keluar command prompt lalu anda masukkan cd instalasi os anda sesuai selera anda. Kemudian cari drive cd-rom atau dvd-rom anda dengan mengetik d: atau e: dan lain sebagainya sesuai lokasi drive cd atau dvd rom anda. Setelah ketemu anda kemudian cari file setup.exe dengan perintah cdnama folfer untuk masuk ke dalam folder. Perintah cd.. untuk mundur satu folder level. perintah dir atau dir/w atau dir/p untuk melihat list file yang ada pada folder tersebut. Kalau sudah ketemu maka jalankan setup.exe atau install.exe dengan mengetik nama file tersebut lalu tekan tombol enter satu kali saja. Langkah berikutnya anda tinggal mengikuti perintah yang ada pada installasi cd atau dvd os.
2. Setting Settingan Boot pada BiosSetelah install ulang windows atau linux selesai, maka keluarkan disket flopyy 1,4 anda dan masuk kembali ke menu bios setelah restart ulang. Pilih IDE-0 sebagai first boot. Floppy bisa anda seting menjadi boot kedua dan cd-rom menjadi boot ketiga. Anda bebas menentukannya sesuai dengan keinginan anda. Sehabis itu direstart ulang kembali.
3. Install Driver dan SoftwareJika sudah berhasil masuk ke tampilan windows atau linux awal, selanjutnya anda nginstall driver untuk sound card, printer, scanner, kabel data, dan sebagainya sesuai hardware yang ada. Anda harus mencari dan memiliki sendiri driver tersebut. Setiap jenis komputer memiliki driver yang berbeda. Biasanya anda akan diberi cd driver saat anda membeli komputer atau hardware lainnya. Tanpa driver maka peralatan yang terhubung pada komputer laptop atau pc tidak dapat berjalan sebagaimana mestinya.
Posted by niney at 6:15 PM 0 comments
Tuesday, April 20, 2010
IP Address
IP is the primary protocol in the Internet Layer of the Internet Protocol Suite and has the task of delivering distinguished protocol datagrams (packets) from the source host to the destination host solely based on their addresses. For this purpose the Internet Protocol defines addressing methods and structures for datagram encapsulation. The first major version of addressing structure, now referred to as Internet Protocol Version 4 (IPv4) is still the dominant protocol of the Internet, although the successor, Internet Protocol Version 6 (IPv6) is being deployed actively worldwide.
Posted by niney at 8:19 PM 0 comments
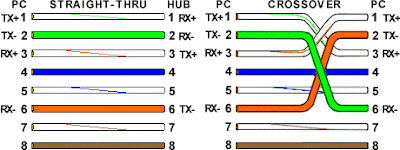
Calour code
Posted by niney at 8:15 PM 0 comments
Cross Cable
Ethernet Cable Instructions:
Pull the cable off the reel to the desired length and cut. If you are pulling cables through holes, its easier to attach the RJ-45 plugs after the cable is pulled. The total length of wire segments between a PC and a hub or between two PC's cannot exceed 100 Meters (328 feet) for 100BASE-TX and 300 Meters for 10BASE-T.
Start on one end and strip the cable jacket off (about 1") using a stripper or a knife. Be extra careful not to nick the wires, otherwise you will need to start over.
Spread, untwist the pairs, and arrange the wires in the order of the desired cable end. Flatten the end between your thumb and forefinger. Trim the ends of the wires so they are even with one another, leaving only 1/2" in wire length. If it is longer than 1/2" it will be out-of-spec and susceptible to crosstalk. Flatten and insure there are no spaces between wires.
Hold the RJ-45 plug with the clip facing down or away from you. Push the wires firmly into the plug. Inspect each wire is flat even at the front of the plug. Check the order of the wires. Double check again. Check that the jacket is fitted right against the stop of the plug. Carefully hold the wire and firmly crimp the RJ-45 with the crimper.
Check the color orientation, check that the crimped connection is not about to come apart, and check to see if the wires are flat against the front of the plug. If even one of these are incorrect, you will have to start over. Test the Ethernet cable.
Ethernet Cable Tips:
A straight-thru cable has identical ends.
A crossover cable has different ends.
A straight-thru is used as a patch cord in Ethernet connections.
A crossover is used to connect two Ethernet devices without a hub or for connecting two hubs.
A crossover has one end with the Orange set of wires switched with the Green set.
Odd numbered pins are always striped, even numbered pins are always solid colored.
Looking at the RJ-45 with the clip facing away from you, Brown is always on the right, and pin 1 is on the left.
No more than 1/2" of the Ethernet cable should be untwisted otherwise it will be susceptible to crosstalk.
Do not deform, do not bend, do not stretch, do not staple, do not run parallel with power cables, and do not run Ethernet cables near noise inducing components
Posted by niney at 8:13 PM 0 comments
















 Kuala Lumpur Time
Kuala Lumpur Time
